- What is Whimsical?
- Getting started with flowcharts
- Getting started with mind maps
- Getting started with wireframes
- Getting started with docs
- What can you do with Whimsical?
- Using Whimsical Boards
- Getting to know Whimsical - video guide 🎥
- Working with Whimsical’s infinite canvas - video guide 🎥
- 5 ways to create a new file
- Getting started with Whimsical AI
- How to create a new workspace
- How to use AI-assisted mind mapping
- Customizing file and folder icons
- Mentions in Whimsical files
- Customizing diagram shapes
- Getting started with sequence diagrams
- Using the command menu
- Commenting in Whimsical files
- Getting started with flowcharts
- Getting started with mind maps
- Getting started with wireframes
- Using Whimsical Boards
- Mentions in Whimsical files
- Customizing diagram shapes
- Using sections on the Whimsical canvas
- Sketch on the canvas with freehand drawing
- Annotating files for more detail
- Text-to-object pasting options
- Adding and displaying links in Whimsical files
- Linking to sections and objects
- How to draw a line
- How to filter selected objects
- Presenting in Whimsical
- Voting on task cards and sticky notes
- Using the timer in boards
- Working with the grid and auto-alignment
- Working with connectors
- Does Whimsical have cloud architecture icons?
- Using tables in Whimsical
- Using sticky notes in boards
- Optimizing performance in larger files
- Embedding external content into Whimsical
- Using spellcheck
- Setting custom thumbnails
- How overlays work in Wireframe mode
- Hiding cursors while collaborating
- Measure between objects in Boards
- Uploading files to Whimsical
- Getting started with sequence diagrams
- Commenting in Whimsical files
- Getting started with docs
- Mentions in Whimsical files
- Text-to-object pasting options
- Adding and displaying links in Whimsical files
- Linking to sections and objects
- Using tables in Whimsical
- Embedding external content into Whimsical
- Using spellcheck
- Changing page width and text size in Docs
- Collapsing text with toggles
- How to create a new workspace
- Requesting file access
- Workspace discovery settings
- Sorting files and folders
- Changing workspace members’ roles
- Adding and removing members
- Creating and managing teams
- Requesting workspace editor access
- Linking between files
- Member roles in Whimsical
- How to delete a workspace
- How to upgrade your workspace
- Guest access
- Renaming your workspace
- Offboarding users
- Consolidating workspaces
- Uploading files to Whimsical
- Organizing your work with tabbed folders
- SAML
- Setting up SAML session expiry
- Security
- Prevent new workspace creation
- Customizing file and folder icons
- How to draw a line
- How to filter selected objects
- Does Whimsical have cloud architecture icons?
- How overlays work in Wireframe mode
- Moving and copying files
- Using Whimsical on mobile
- Does Whimsical have a dark mode?
- File version history
- Why are the colors of some elements toned down?
- Does Whimsical support offline mode?
- Teams, workspaces & sections explained
- Does Whimsical work on iPad?
- Free viewers commenting in workspaces
- Syntax highlighting in code blocks
- Whimsical desktop app
- Is Whimsical available in other languages?
- Inverting the zoom direction in Whimsical so it works more like Sketch
- Troubleshooting issues and reporting bugs
- How to add emojis
- Team FAQs
- How to restore deleted files from the trash
- Searching in your Whimsical workspace
- Organizing files in your workspace
- I’ve upgraded but still don’t have access to the paid features
- Why can't I edit my files?
- Reporting content in Whimsical
- Does Whimsical have an affiliate or referral program?
- Collaborating with others in real time
- Sharing files and managing access permissions
- Hiding cursors while collaborating
- How to switch between workspaces
- Sharing feedback and feature requests
- Embedding & integrating boards with Jira Issues
- Integrating Whimsical with Google Docs
- Embedding files in ClickUp views
- Embedding files in Asana
- Embedding Whimsical files
- Whimsical AI Diagrams for ChatGPT
- Creating Jira & Confluence Smart Links for Whimsical Files
- Embedding files in Guru
- Embedding files in Trello
- Embedding & integrating boards in Notion
- Integrating Whimsical and GitHub
- Embedding files in Zendesk
- Support Whimsical embeds in your app with EmbedKit
- Whimsical previews and notifications in Slack
- Embedding files in Canva
- Integrating Whimsical and Linear
- Embedding files in Nuclino
- Embedding files in Monday
- Embedding files in Medium
- Embedding files in Slab
- Embedding files in Coda
- Whimsical API (Beta)
- SAML
- SAML SSO in Whimsical
- SAML SSO with Okta
- SAML SSO with Auth0
- SAML SSO with OneLogin
- SAML SSO with Microsoft Entra ID (Azure AD)
- SAML SSO with Google Workspace (previously G-Suite)
- SAML SSO with Active Directory Federation Services (ADFS)
- SAML SSO with other identity providers
- Setting up SAML session expiry
- Managing email changes with SAML and SCIM
- SCIM
- Setting up SCIM with Okta
- Setting up SCIM with JumpCloud
- Setting up SCIM with Entra ID (Azure AD)
- SCIM provisioning with Groups in Okta
- SCIM user provisioning in Whimsical
- SCIM provisioning with Groups in Entra ID (Azure AD)
- Security
- Setting up Two-factor Authentication (2FA)
- Prevent new workspace creation
- Whitelisting Whimsical domains
- Signing in with your Whimsical account on multiple devices
- Contact us
SAML SSO with Active Directory Federation Services (ADFS)
Whimsical supports SAML-based Single Sign-On (SSO) for enterprise authentication, allowing organizations to integrate with identity providers (IdPs) like Active Directory Federation Services (ADFS). This guide provides a step-by-step walkthrough for configuring ADFS to enable SSO with Whimsical.
Note: SAML SSO is only available on our Business and Enterprise plans. You must be an admin to enable SAML SSO.
Before configuring ADFS SSO with Whimsical, ensure you have:
- Administrator access to your ADFS instance.
- ADFS running on Windows Server with a public HTTPS endpoint.
- A custom domain to associate with your SSO configuration.
Step 1: Add a relying party trust in ADFSCopied!Link to this section
- Open the ADFS Management Console.
- Go to Relying Party Trusts and select Add Relying Party Trust.
- Choose Claims Aware and click Start.
- Select Enter data about the relying party manually and click Next.
- Provide a Display Name (e.g., "Whimsical") and click Next.
- Select AD FS profile (SAML 2.0) and click Next.
- Skip the certificate setup by clicking Next.
- Under Configure URL, check Enable support for the SAML 2.0 WebSSO protocol.
- Enter the Whimsical ACS (Assertion Consumer Service) URL:
https://whimsical.com/sso/saml/consumethen click Next. - Enter the Whimsical ACS URL here also, under Relying Party Trust Identifier
- Click Add, then Next.
- Choose an access control policy, and click Next.
- Click Next again to complete the setup, then Close.
Step 2: Configure claim rulesCopied!Link to this section
- In ADFS Management Console, select the newly created Whimsical relying party trust.
- Click Edit Claim Issuance Policy.
- Click Add Rule and choose Send LDAP Attributes as Claims.
- Set the rule name to "LDAP to SAML Attributes".
- Select Active Directory as the Attribute Store.
- Map the following attributes:
- E-Mail-Addresses → Name ID
- Given-Name → FirstName
- Surname → LastName
- Click Finish.
- Click Add Rule again, select Transform an Incoming Claim, and click Next.
- Set Incoming claim type to Name ID.
- Set Outgoing claim type to Name ID and Outgoing name ID format to Email.
- Click Finish and Apply the changes.
Step 3: Obtain federation metadata URLCopied!Link to this section
- In ADFS, navigate to Service > Endpoints.
- Find the Federation Metadata document URL, which usually looks like:
https://your-adfs-server/FederationMetadata/2007-06/FederationMetadata.xml - Copy this URL as it will be required in Whimsical.
Step 4: Configure Whimsical SSO settingsCopied!Link to this section
First, go to Workspace settings, which you'll find under your workspace name in the top left corner:
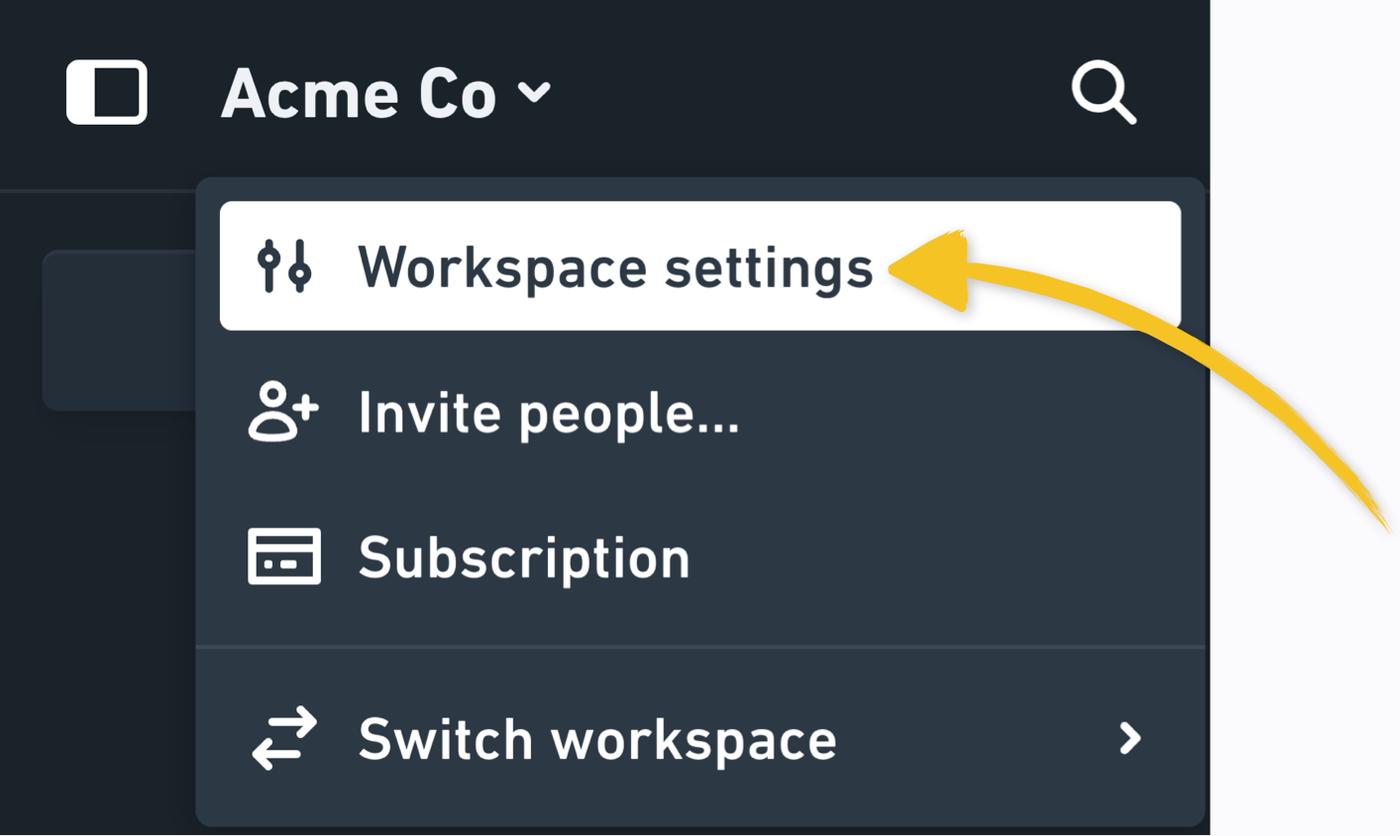
Then, enable SAML SSO. Once it's enabled:
- Enter your ADFS Metadata URL (from Step 3).
- Set the required attributes (NameID, FirstName, LastName) to match your ADFS claim rules.
- Enable SSO and test the configuration.
Step 5: Test and troubleshootCopied!Link to this section
- If logging in with ADFS fails:
- Check ADFS logs for errors.
- Ensure Name ID and attribute mappings are correct.
- Verify that the ADFS metadata URL is accessible.
If you have any trouble getting this set up, please reach out to our Support team. We're always happy to help. 😉
